When you need to deploy code in a function app using terraform you can use the zip_deploy_file parameter. Using this you can specify a zip file that will be created from your committed code and by doing so you can dynamically deploy code using terraform.
The first thing that you will need to do is to create a folder with the code that you want to commit in the function_app. In my example I have the terraform files inside the aws and azure folders and in the same directory I have a folder called resources where the code is located. This code need to be deployed in the serverless function app.
Create a data archive_file with terraform and specify where your code is located. You should correctly point where the files are stored.
data "archive_file" "python_function_package" {
type = "zip"
source_file = "../resources/function.py"
output_path = "function.zip"
}
Then you should use the above data archive and use it along with zip_deploy_file.
resource "azurerm_linux_function_app" "functionapp" {
name = var.serviceplan_name
resource_group_name = azurerm_resource_group.rg.name
location = azurerm_resource_group.rg.location
storage_account_name = azurerm_storage_account.sg.name
storage_account_access_key = azurerm_storage_account.sg.primary_access_key
service_plan_id = azurerm_service_plan.serviceplan.id
zip_deploy_file = data.archive_file.python_function_package.output_path
app_settings = "${var.app_settings}"
site_config {
application_stack {
python_version = "3.10"
}
}
}
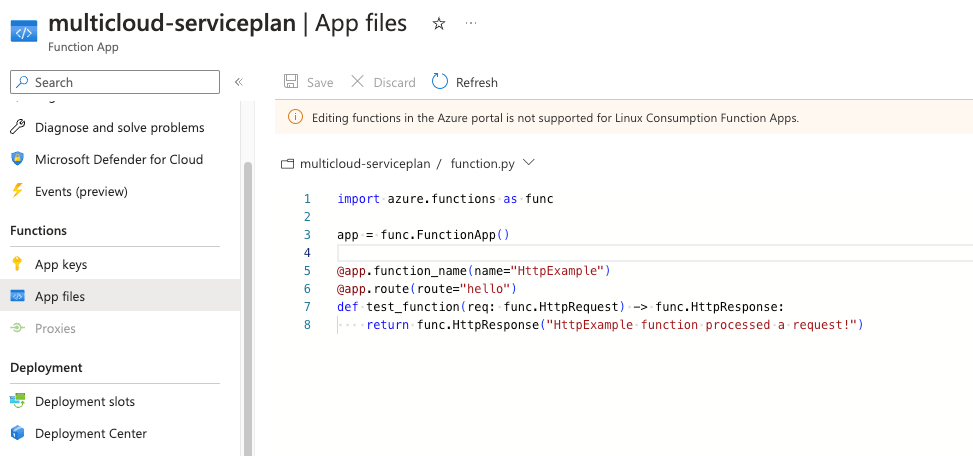
When you deploy your terraform code the function app will correctly upload the code in your infra component and you can check that by navigating inside the code on azure portal.
azurerm_linux_function_app | Resources | hashicorp/azurerm | Terraform | Terraform Registry