As security is one of the most important things on your infrastructure, you should enable logging for all commands and actions that a user performs (logins included).
In this article I will explain the procedure using auditd which comes preinstalled with many Linux distributions.
First things first, check if auditd is already installed and started on your system.

Then go to the rules file and open it with your favorite editor.
vi /etc/audit/rules.d/audit.rules
Add the below two rules to the end of the file.
-a exit,always -F arch=b32 -S execve -k auditcmd
-a exit,always -F arch=b64 -S execve -k auditcmd
Then execute on terminal:
augenrules You should then restart the service. Trying to do so with systemctl you may encounter the below error:

Execute auditd stop and start using the below commands:
service auditd stop
service auditd start

Verify existing rules:
auditctl -l

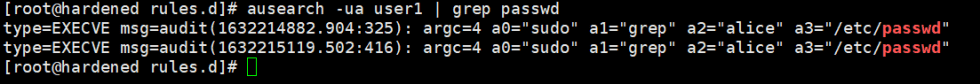
You are now ready and you can test the logging functionality. Perform a sudo action with a non root user.

Locate the action from logs.